.svg)
Eliminate Blind Spots Across Your Digital Perimeter

to your company!
01. Continuous Asset Discovery
Automatically uncover all exposed infrastructure, including shadow IT.


Comprehensive mapping: Scan your entire external perimeter, including known and unknown assets.

Shadow IT detection: Spot unauthorized infrastructure deployed outside IT’s control.

Zero setup: No agents, sensors, or internal access required.
.svg)
02. Real-Time Monitoring & Alerts
No more manual remindersGet instant notifications when assets appear, disappear, or change. or outdated files.


Live tracking: Monitor for new IPs, expired certificates, open ports, and configuration drifts.

Instant alerts: Get notified of critical changes before attackers can exploit them.

Automated context: Each asset comes with metadata, history, and risk context out of the box.
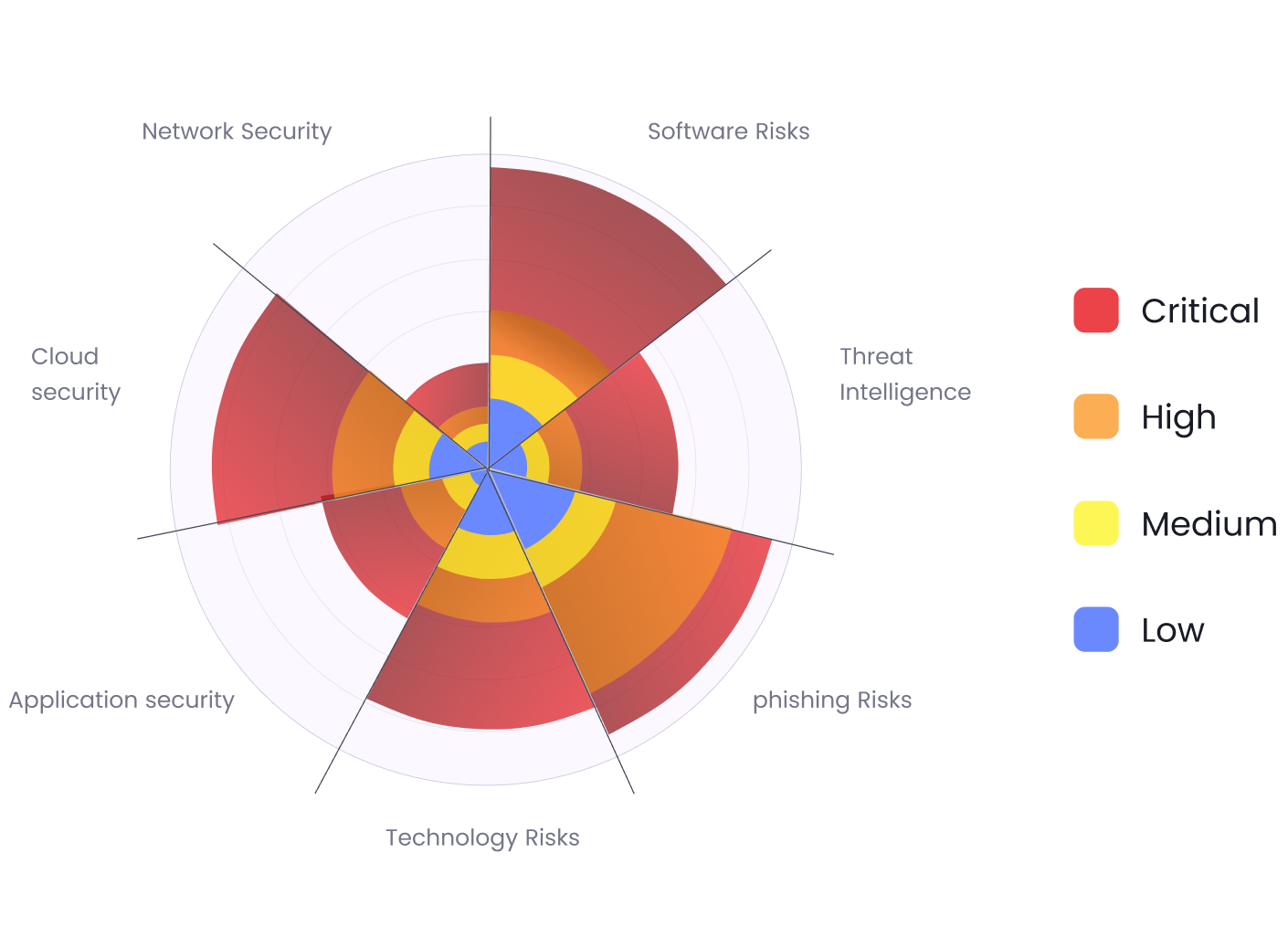
03. Risk Prioritization
Focus remediation on high-risk vulnerabilities, not false positives.


Vulnerability-aware scoring: Evaluate exposures based on exploitability and business impact.

Noise reduction: De-duplicate findings across subsidiaries, domains, and services.

Remediation triggers: Automatically assign tasks or open tickets for high-priority issues.
.svg)
01. Continuous Asset Discovery
Automatically uncover all exposed infrastructure, including shadow IT.


Comprehensive mapping: Scan your entire external perimeter, including known and unknown assets.

Shadow IT detection: Spot unauthorized infrastructure deployed outside IT’s control.

Zero setup: No agents, sensors, or internal access required.

02. Real-Time Monitoring & Alerts
Get instant notifications when assets appear, disappear, or change.


Live tracking: Monitor for new IPs, expired certificates, open ports, and configuration drifts.

Instant alerts: Get notified of critical changes before attackers can exploit them.

Automated context: Each asset comes with metadata, history, and risk context out of the box.
.svg)
03. Risk Prioritization
Focus remediation on high-risk vulnerabilities, not false positives.


Vulnerability-aware scoring: Evaluate exposures based on exploitability and business impact.

Noise reduction: De-duplicate findings across subsidiaries, domains, and services.

Remediation triggers: Automatically assign tasks or open tickets for high-priority issues.
.svg)
“We discovered more than 40 forgotten assets across our subsidiaries in the first scan. UEM immediately closed visibility gaps.“
CIO, Industrial Group
Ready to see for yourself?
Test drives all platform features for yourself. No commitment and No credit card!
.svg)



.svg)
.svg)
.svg)

.svg)
.svg)

.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)


.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)












