Prove Operational Resilience. Automatically
.svg)
to your company!
01. DORA-Mapped Risk Workflows
Assess, score, and monitor ICT third-party risk with fully automated flows.


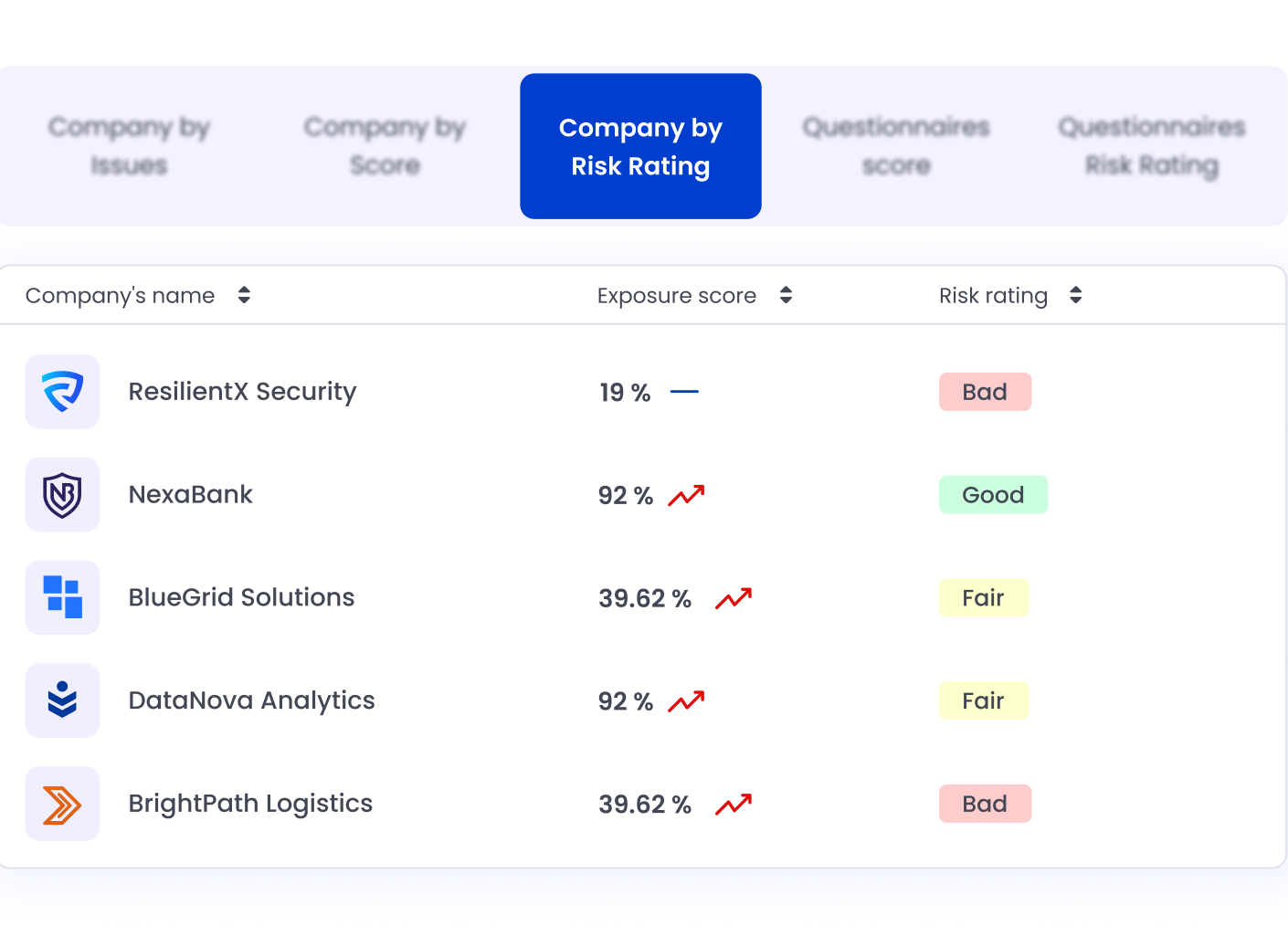
Custom Risk Scoring: Evaluate vendors by impact on ICT operations, aligned with DORA obligations.

Automated Due Diligence: Trigger onboarding, annual reviews, and remediation workflows. No manual tracking.

Evidence Collection: Log every assessment and control in one place, ready for supervisory authorities.
.svg)
02. Operational Resilience Monitoring
Stay ahead of disruptions and security gaps across your supply chain.


Continuous Posture Checks: Monitor cloud, code, and perimeter risks in real time.

Third-Party Drift Detection: Get alerts when vendor security posture deteriorates or exposure changes.

Vendor Outage Visibility: Detect and log outages or critical service degradation across your ICT chain

Centralized Audit Logs: Every action and change is tracked and exportable for regulators.

Real-Time Compliance Dashboards: Visualize control coverage and vendor status instantly.

On-Demand Reports: Generate documentation mapped to DORA articles with a single click.

01. DORA-Mapped Risk Workflows
Assess, score, and monitor ICT third-party risk with fully automated flows.


Custom Risk Scoring: Evaluate vendors by impact on ICT operations, aligned with DORA obligations.

Automated Due Diligence: Trigger onboarding, annual reviews, and remediation workflows. No manual tracking.

Evidence Collection: Log every assessment and control in one place, ready for supervisory authorities.

02. Operational Resilience Monitoring
Stay ahead of disruptions and security gaps across your supply chain.


Continuous Posture Checks: Monitor cloud, code, and perimeter risks in real time.

Third-Party Drift Detection: Get alerts when vendor security posture deteriorates or exposure changes.

Vendor Outage Visibility: Detect and log outages or critical service degradation across your ICT chain
.svg)

Centralized Audit Logs: Every action and change is tracked and exportable for regulators.

Real-Time Compliance Dashboards: Visualize control coverage and vendor status instantly.

On-Demand Reports: Generate documentation mapped to DORA articles with a single click.

“ResilientX Security made our DORA readiness painless.It helped us cut vendor risk while staying compliant.“
Compliance Officer, European Asset Manager
Ready to see for yourself?
Test drives all platform features for yourself. No commitment and No credit card!
.svg)



.svg)
.svg)
.svg)

.svg)
.svg)

.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)


.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)












